Mikrotik Router L2TP Client Configuration Steps
L2TP, or Layer 2 Tunneling Protocol, is a widely used protocol that allows for the creation of virtual private networks. It is often used to connect remote workers to a company's private network, allowing them to access files and resources as if they were on-site. In this case we are leveraging L2TP as our transport overlay to get to the Full Span Solutions Core Transit hub router closest to you. L2TP works well because it allows your system to initiate the connection whereas GRE is stateless and would require your system to be reachable without first initiating a connection. This allows L2TP to work from behind NAT on private networks on CG-NATed provider networks.
In this configuration example, we will be using a topology that looks like this: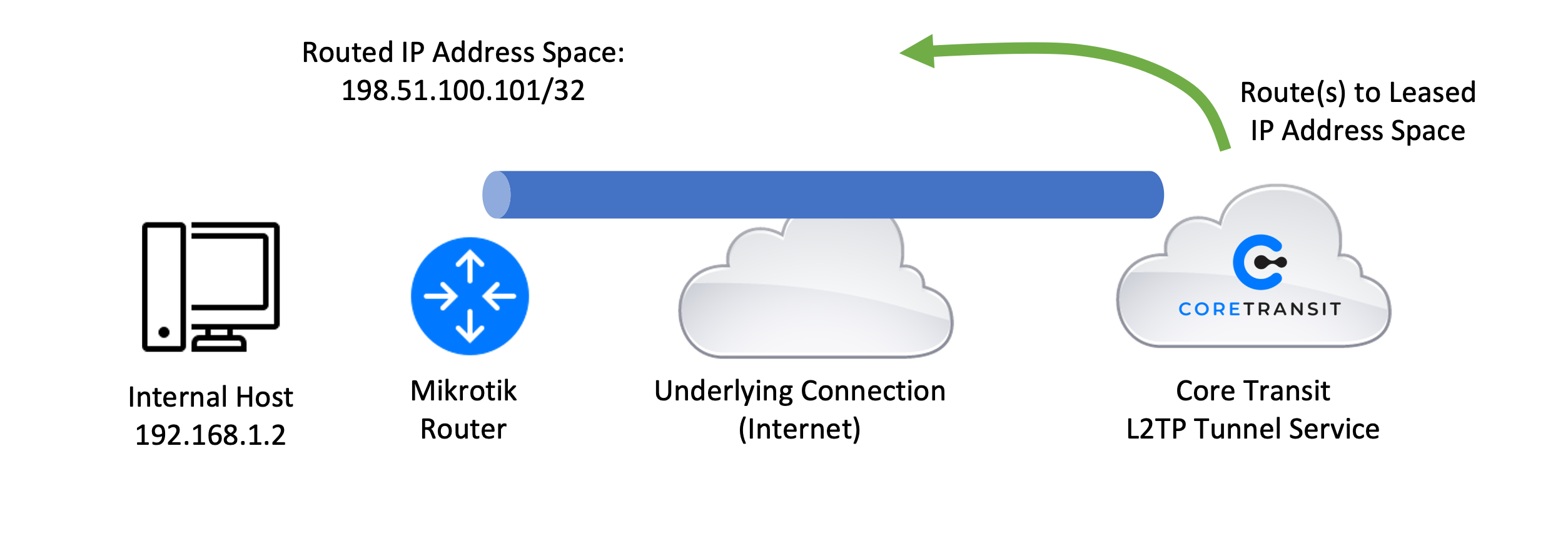
Prepare routing and interface settings
If your device is learning its WAN IP address via DHCP you will need to take these steps before configuring an L2TP interface. If you will be using this L2TP tunnel for internet traffic, which will likely include a default route, it is important to ensure we prevent a routing loop with the existing physical interface.
- Log in to your Mikrotik router's web interface or connect to it using Winbox.
- On the left click “IP”, then “DHCP Client”. Next, select the router interface where your device is learning its address via DHCP.
- Search for “Default Route Distance” and adjust this value from the default of 1 to something higher. 10, for instance.
The configuration would look something like this assuming ether1 is your external interface.
/ip dhcp-client
add comment=defconf default-route-distance=10 interface=ether1Configure the L2TP client on the Mikrotik router
Once you have the necessary information from the L2TP server administrator, you can begin configuring the L2TP client on the Mikrotik router. To do so, follow these steps:
- Log in to your Mikrotik router's web interface or connect to it using Winbox.
- Click on the PPP menu on the left.
- Under the Interfaces tab, select Add New and the L2TP Client option.
- Adjust the following settings with the information you received.
- Connect To: This is the hostname or IP address of the L2TP Server
- Username: Username provided. This may or may not be the same as your Core Transit account username/email address.
- Password: This is the L2TP tunnel password. This will NOT be the same as your Core Transit account password.
- Add Default Route: Check this option if you will be using this service for all internet traffic.
- Default Route Distance: This should be lower than the value set in Section 1.
- At this time we are not supporting encryption as all traffic is untrusted internet traffic. Other security measures such as SSL/TLS, a client VPN, etc should be used if data privacy is needed with your traffic.
- Click the Apply button to save the L2TP client configuration.
What does this look like from the CLI? Glad you asked! Here is a tested working config snipped as well:
#L2TP Client configuration
/interface l2tp-client
add add-default-route=yes connect-to=peering1.dfw1.coretransit.io disabled=no name=l2tp-out1 password="yourtunnelpassword" profile=default user=yourtunnelusernameTest the L2TP connection
Once you have configured the L2TP client on the Mikrotik router, you should test the connection to ensure that it is working correctly. To do so, follow these steps:
- Go to the Interfaces menu and select the L2TP client connection you just created.
- Disable and enable the L2TP interface to force L2TP to establish the L2TP connection to the server.
- Wait for the connection to be established.
- Check the Status field to ensure that the connection is established.
- If the connection is not established, review your L2TP client configuration and ensure that the information provided by the L2TP server administrator is correct.
#Configure a description for interface names
/interface ethernet
set [ find default-name=ether1 ] comment="Link to Starlink, etc"
set [ find default-name=ether4 ] comment="Downlink to customer network"
#L2TP Client configuration
/interface l2tp-client
add add-default-route=yes connect-to=peering1.dfw1.coretransit.io disabled=no name=l2tp-out1 password="yourtunnelpassword" profile=default user=yourtunnelusername
#set IP details of the LAN interface toward your devices if we are routing you a /30 or greater block
#198.51.100.0/30 is an example /30. Replace it with your own.
/ip address
add address=198.51.100.1/30 interface=ether4 network=198.51.100.0
#Gets a DHCP address from the upstream provider
/ip dhcp-client
add comment="Starlink Internet Connection" interface=ether1
#use this mss configuration to help address mtu issues
/ip firewall mangle
add action=change-mss chain=forward new-mss=1400 out-interface=all-ppp passthrough=yes protocol=tcp tcp-flags=syn tcp-mss=1301-65535
NAT Configuration
Core Transit is designed to be flexible in that we can offer multiple IPv4 addresses as /32, /31, /30, etc, routes to your network. A /32 of course cannot be used on an ethernet LAN but it can be assigned to a loopback or leveraged for NAT with great flexability. For NAT the address doesn't need to be assigned to an interface. This can be a little intimidating to some users but it doesn't need to be!
In the Web UI or Winbox you can navigate to IP > Firewall > NAT to build a NAT rule.
Under the General section and "Chain" option select "scrnat" in the dropdown.
Next, go to the "Action" section and select "scr-nat" from the "To Address" dropdown. In this example 198.51.100.101/32 is routed toward our system by Core Transit so we will use 198.51.100.101 as the address here. You can optionally constrain this NAT statement further by defining internal and external interfaces, blocks of LAN IPs, etc. Mikrotik NAT configuration is very flexible to the point where you could send some traffic over the L2TP tunnel and some over the physical WAN interface by manipulating NAT rules. Without further conditions, the NAT rule would look like this:
ip firewall nat
add action=src-nat out-interface=l2tp-out1 chain=srcnat comment="NAT to IP routed to us by Core Transit" to-addresses=198.51.100.101Video Walkthrough
Still have questions? In this video we walk through the steps above in the web UI of the Mikrotik platform as well.
https://www.youtube.com/watch?v=EPoesD0Tfok
IPv6
Core Transit will also route a /60 IPv6 prefix toward your system over the L2TP tunnel. This /60 is a prefix deligation that you can then assign inside your network to assign to hosts, etc.
#Configure IPv6 to request a prefix from Core Transit.
/ipv6 dhcp-client
add add-default-route=yes interface=l2tp-out1 pool-name=testv6 prefix-hint=::/60 request=prefix
#Configure an IPv6 address on your internal interface toward clients. In this case its the"bridge" interface
/ipv6 address
add address=::/64 from-pool=testv6 interface=bridge
#Configure your internal interface and add DNS servers
/ipv6 nd
add dns=2001:4860:4860::8888,2001:4860:4860::8844 hop-limit=64 interface=bridge
Conclusion
Configuring a L2TP client connection on a Mikrotik router connecting to an L2TP server requires just a few steps, but it is critical to ensure that the configuration is correct to establish a reliable connection. Following the steps outlined in this technical article will help you set up an L2TP client connection on your Mikrotik router and ensure that your remote workers can access your private network securely. If you have trouble you can open a case for further assistance.



























