Below is an example of how to configure a Mikrotik router with a Core Transit tunnel where you want to specifically route egress traffic out of the tunnel while all other traffic exits on the underlying connection. The most common example of this would be a direct assignment of IP addresses to internal hosts that might be hosting a service over the tunnel alongside hosts that don’t need to leverage the tunnel at all.
In this example, we make a few assumptions that will differ in your environment.
- The example routed address space is 192.2.0.0/29
- A separate routing table will be created, we call it “coretransit”
- The L2TP interface in our example is called l2tp-out1.
- It's also assumed you have familiarity with IP routing and the Mikrotik Router OS 7 platform.
The topology of the example will look like this:
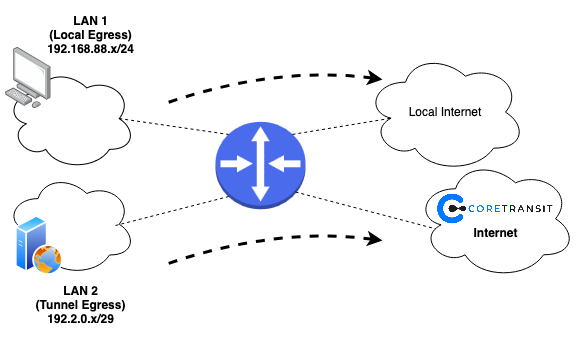
Create the L2TP Client Connection
Assuming you're using an L2TP client to connect to a Core Transit, the configuration would look similar this:
/interface l2tp-client
add connect-to=peering1.dfw1.coretransit.io user="your_username" password="your_password" name="l2tp-out1"
Verify the tunnel comes up and is active. You will not want it to add a default route as is the case in some of our other examples.
Create the coretransit Routing Table
Define a new routing table named coretransit. This table will contain the routes used for the policy-based routing:
/routing table add name=coretransitConfigure the Routes in the coretransit Table
Next, we configure the necessary routes in the coretransit routing table. This could include default routes or specific routes that should be routed through the L2TP interface. Keep in mind that routing is stateless so any traffic that comes into your router will need a route back to its originator for connections to be established.
For example, if you want all outbound traffic from your routed address block to go through the L2TP interface (l2tp-out1), you would add a default route to the coretransit table:
/ip route
add dst-address=0.0.0.0/0 gateway=l2tp-out1@main routing-table=coretransitAdd a Policy Route
Now, let's configure the policy route that will route the traffic from 192.2.0.0/29 into the l2tp-out1 interface and use the coretransit routing table.
/routing rule
add action=lookup-only-in-table disabled=no src-address=192.2.0.0/29 table=coretransitThis rule tells the router to use the coretransit routing table for any traffic originating from the 192.2.0.0/29 subnet. Note that these rules are very specific and are processed before other routing logic. This means that traffic coming from 192.2.0.0/29 won’t be able to reach connected routes, etc. from the global table unless you specifically permit it above the rule we defined above. To demonstrate this here we added a rule to ensure that the 192.2.0.0/29 hosts can reach the 192.168.88.x/24 subnet.
/routing rule
add action=lookup-only-in-table dst-address=192.168.88.0/24 table=main
add action=lookup-only-in-table disabled=no src-address=192.2.0.0/29 table=coretransit


























